By Dolly Sharma.Dec 4, 2022
In this blog post, let’s walk through the detailed steps of configuring the connectivity between Google Cloud Platform (GCP) and Azure using VPN so that you can migrate your workloads from Azure to GCP or run multi cloud workloads across both the platforms.
Before you begin
- An Azure account with an active subscription and a project on GCP.
- Make sure you have necessary admin roles to perform the below activities as per these links: GCP and Azure.
- VPC Network (Virtual Network on Azure) and subnets are already created in both GCP and Azure.
- On GCP, the firewall rule must be added for traffic flow (ingress and egress) between Azure and GCP.
- On Azure, the Security Group should be configured for traffic flow and subnet propagation.
- External facing public IPv4 address for your VPN device.
Topology
Here’s a diagram that showcases the connectivity between GCP and Azure along with the various components that make it work.
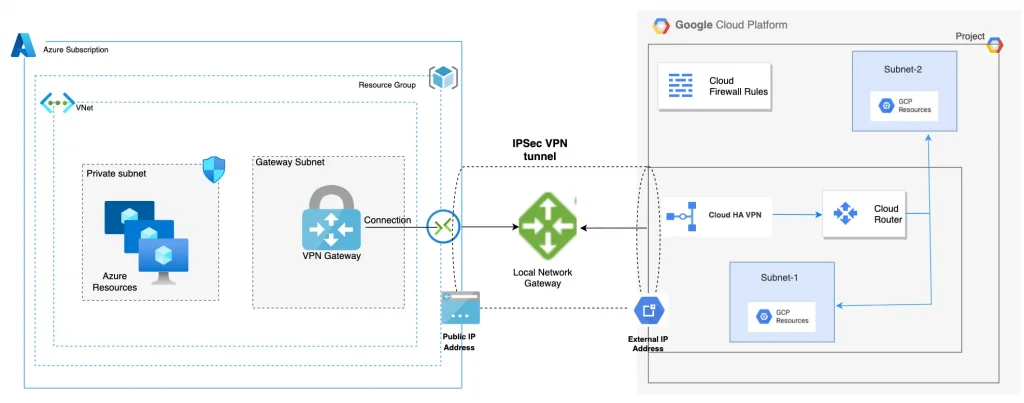
- Google Cloud VPC network: A single virtual network within a single Google Cloud project.
- External IP address or Google Cloud peer address: External IP addresses used by peer VPN devices to establish HA VPN with Google Cloud. External IP addresses are allocated automatically, one for each gateway interface within a Google Cloud project.
- Dynamic Routing: Google Cloud dynamic routing for VPN using the Border Gateway Protocol (BGP). Note that HA VPN only supports dynamic routing.
- HA VPN: This is a High Availability Cloud VPN that lets us securely connect on-premises networks to our private networks on GCP through an IPsec VPN connection.
- Virtual Network Gateway: Azure VPN gateways provide cross-premises connectivity between customer premises and Azure. we deploy our Virtual Network Gateway, which will be used to create a VPN tunnel to our Google environment. This will be deployed into the “GatewaySubnet”
- Site-to-Site (IPsec): Composed by a `VPN Gateway`, a `Local Gateway` and a `Connection`, allows to send encrypted traffic between an Azure’s VNet and an on-premises location through the public internet.
Hands On
Let’s now implement the VPN tunnel at both ends.
- Sign in to the Azure portal
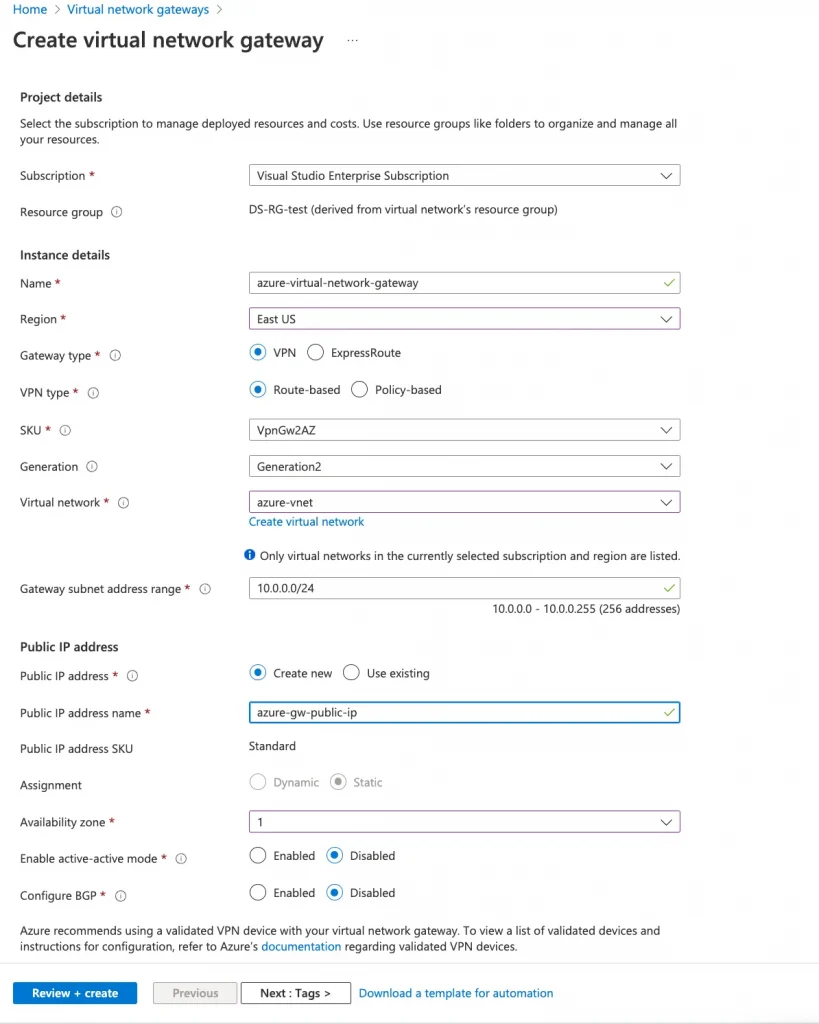
- Create a Virtual Network Gateway
2. Next, I create a VPN connection on GCP. First, I select the type of VPN connection as high availability (HA),
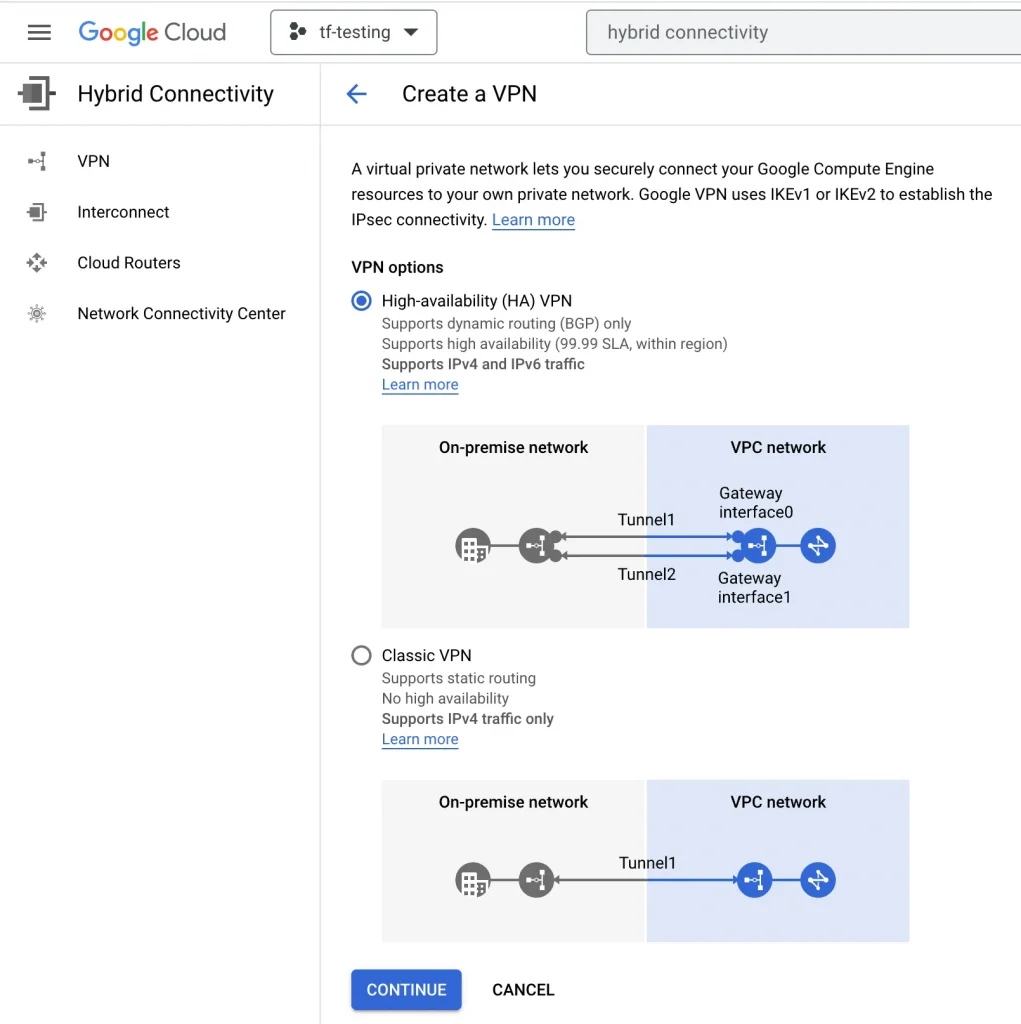
Then I create a Cloud HA VPN gateway. I provide a name (gcp-vpn-gateway), a VPC (vpc-1), and a Region (us-east1).
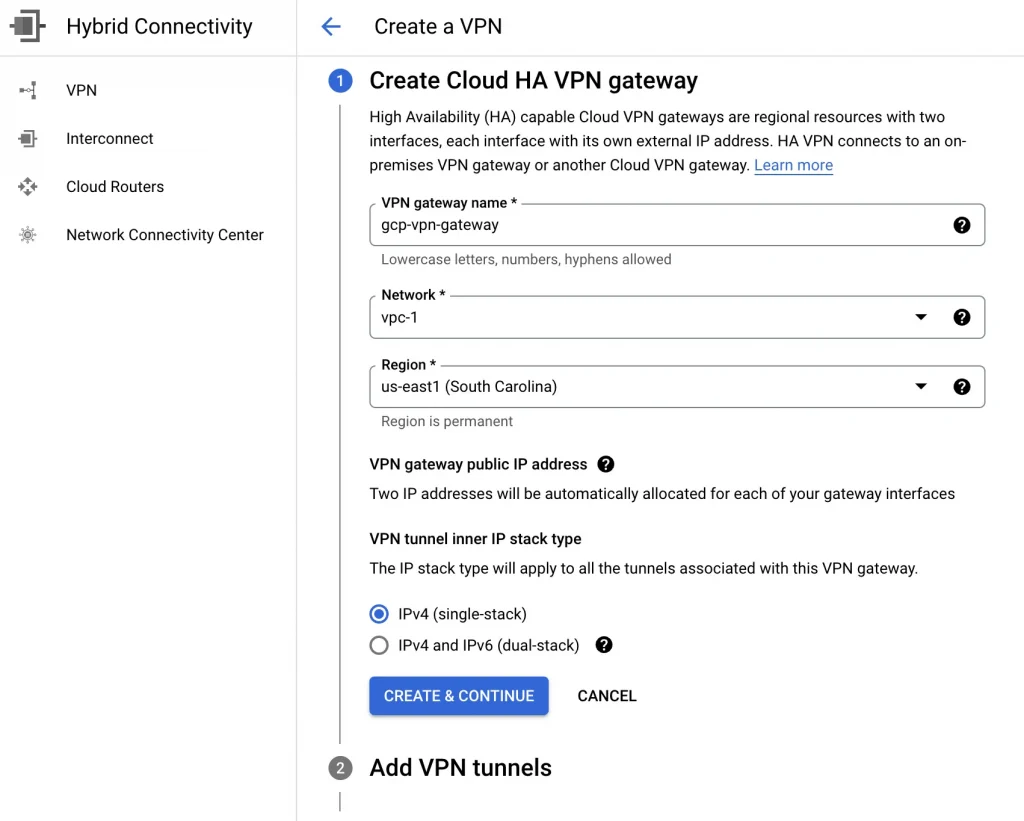
3. After the VPN gateway is created, it is assigned two public IP addresses. Take note of the IPs because we will use them later.
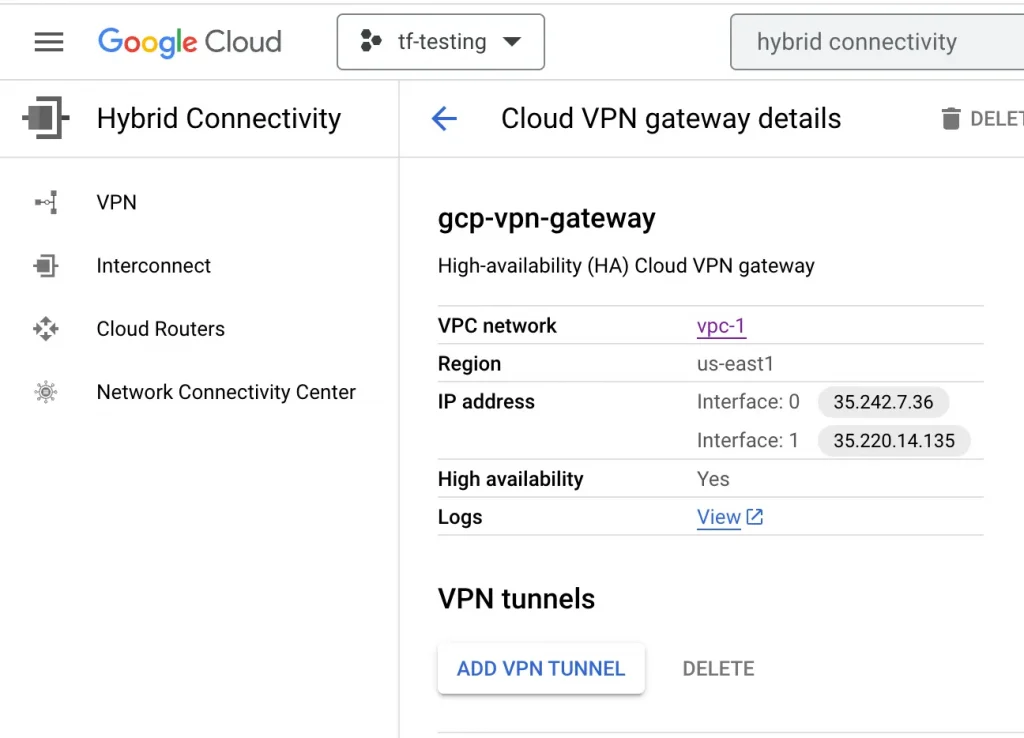
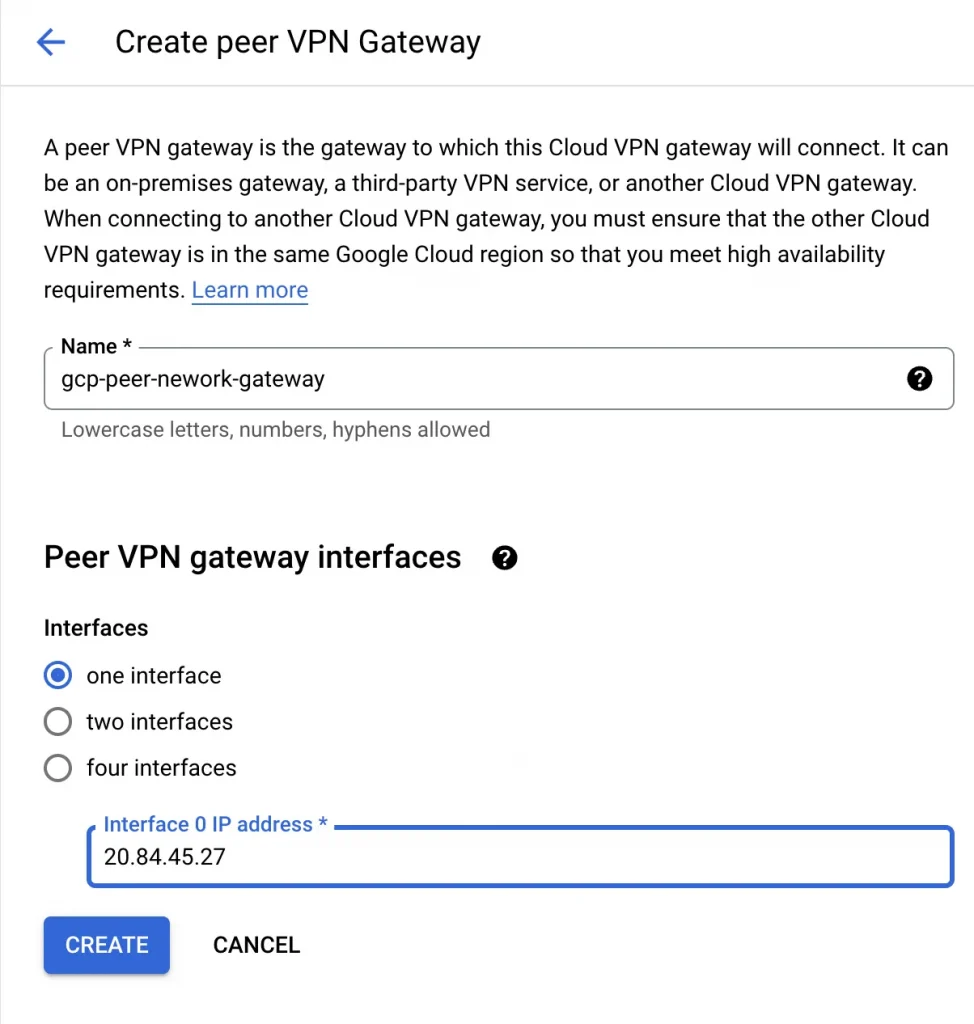
4. Now let’s create the peer configuration. I select Add a peer VPN gateway and choose one interface. Under Peer VPN gateway interfaces, for Interface 0 IP Address, I add the IP address of the Outside Virtual Private Gateway created earlier.
You can follow the same steps to add additional tunnels for High Availability or added capacity.
Create Peer VPN gateway:
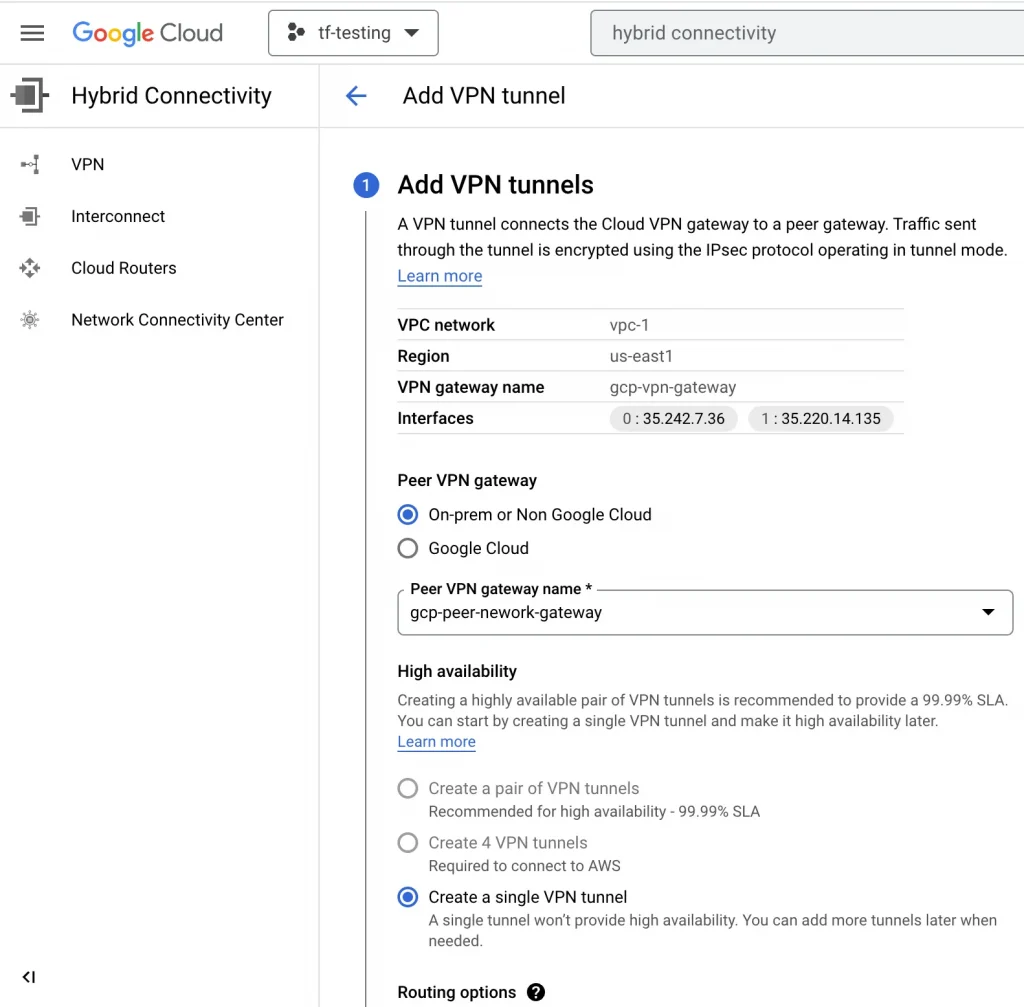
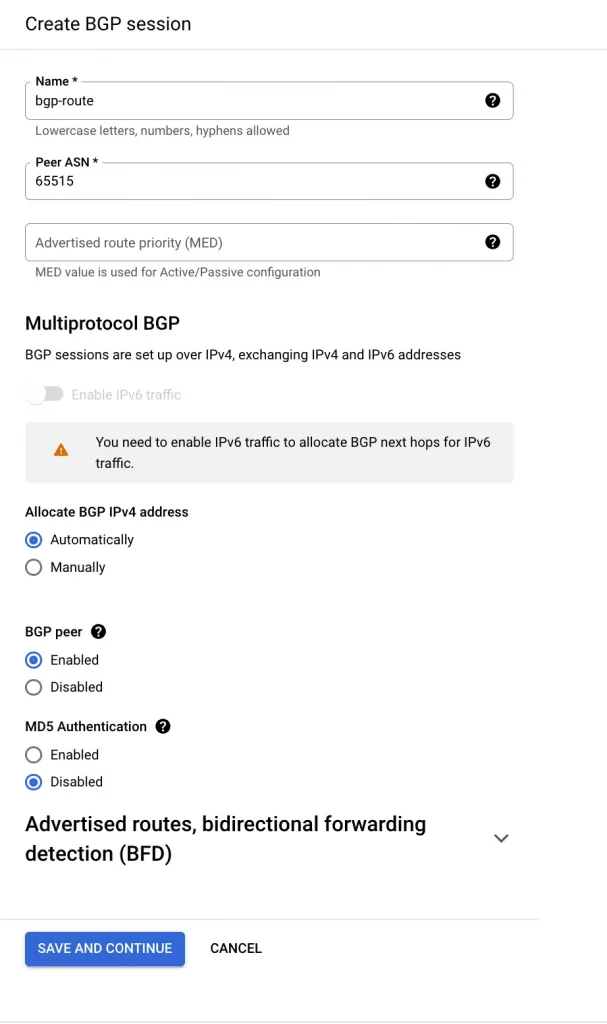
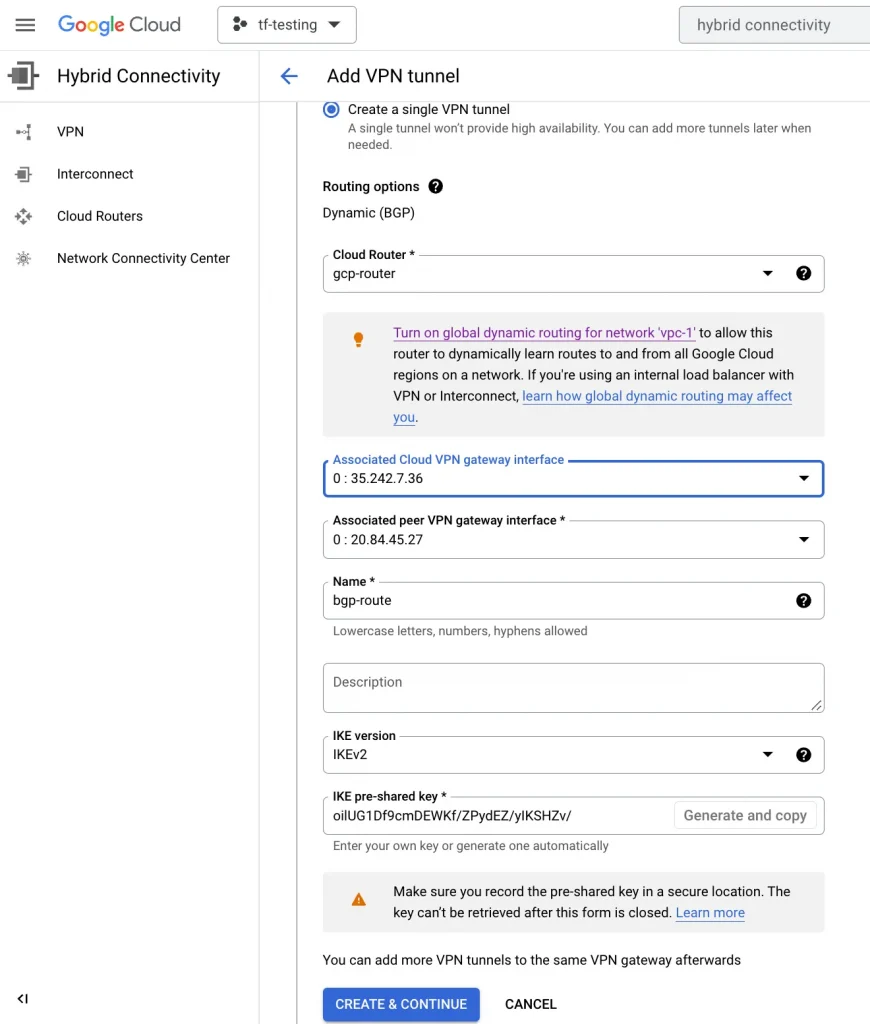
4. Next, I select ADD VPN TUNNEL and configure the BGP session.
4. On GCP create BGP session
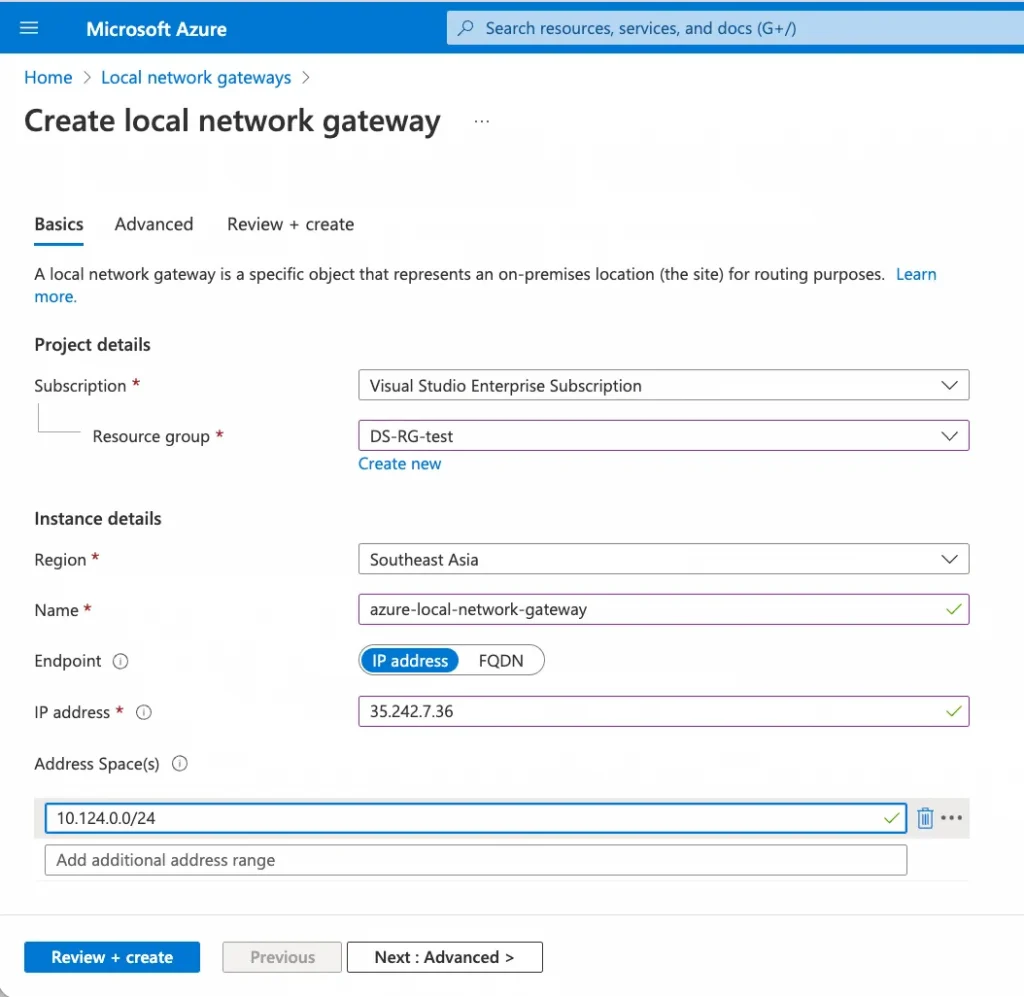
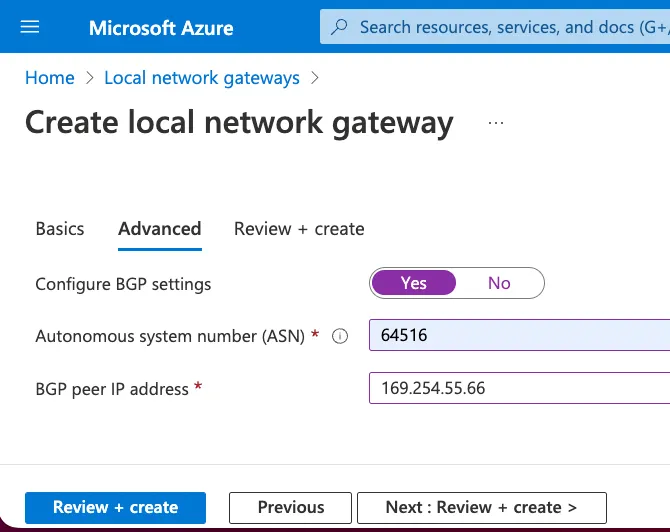
5. Create Local Gateway Network with GCP information
I create a local network gateway with gcp information, we can repeat the same steps for the second local network gateway by providing the second IP address High Availability or added capacity.
6. Create a connection using Virtual Network Gateway and Local Network Gateway
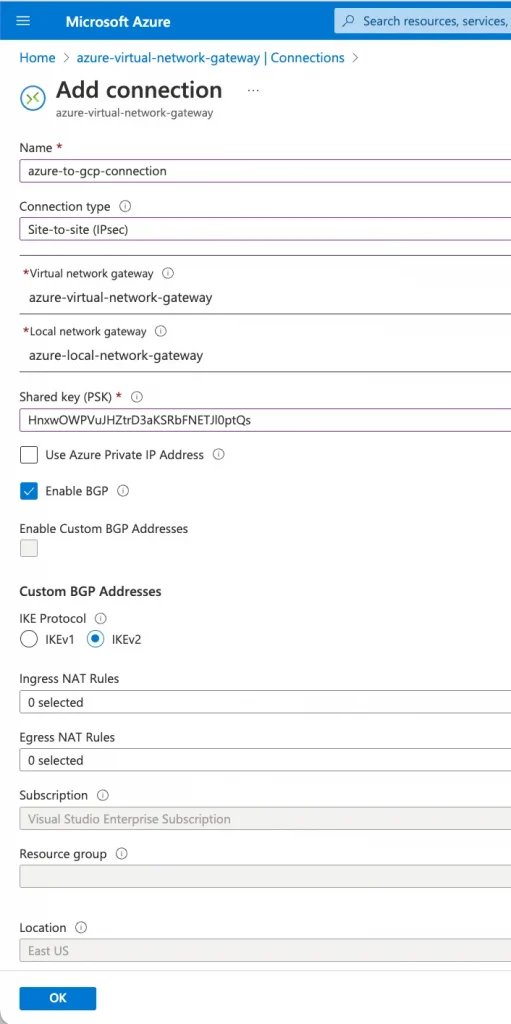
7. Validate Connectivity
At this point, your VPN connection should show one tunnel with the status Established.
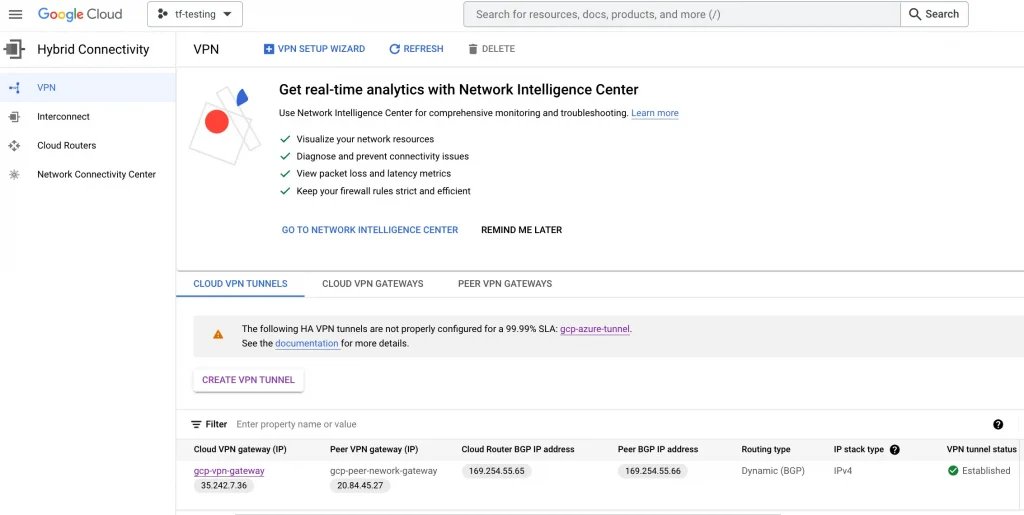
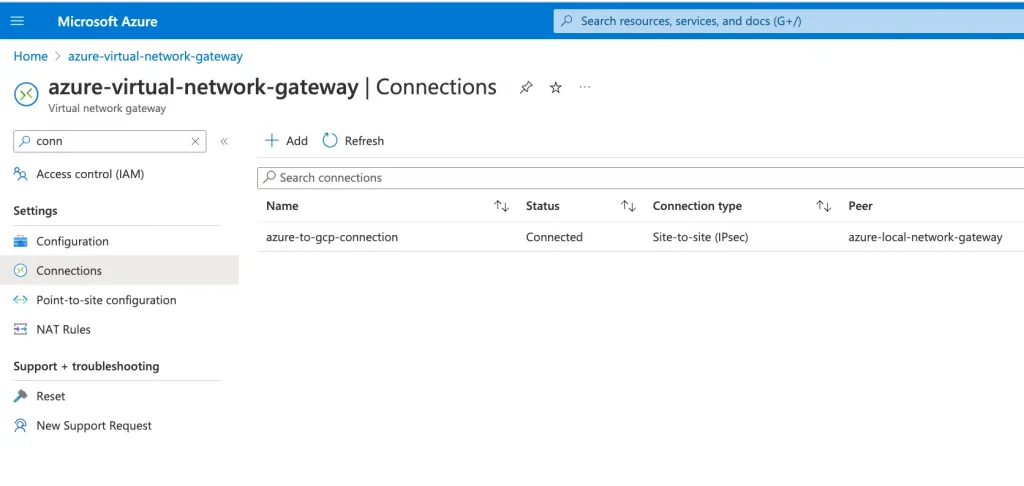
Go back to Azure and verify that the connection status is showing connected.
Conclusion
In this blog, we have learned about the prerequisites for creating the Site to Site VPN between Azure and GCP. Also, we have discussed the detailed steps for creating IPSec VPN tunnel between Azure and GCP
Best Practices
Limitations
References
The original article published on Medium.
