By Tanmay Bangale.Dec 20, 2022
In this article, we will be looking at how to configure a SAML Identity Provider (Auth0 in this case) for signing in to Apigee’s Integrated Developer Portal.
The conventional way to sign in to an Apigee Integrated Developer Portal is through the Built-in Identity Provider option. It requires users to pass their credentials (username and password; user registration should be done if not an existing user) to the integrated portal for authentication. When you create a new portal, the built-in identity provider is configured and enabled. To understand the sign-in experience from the user perspective, see Signing in to the portal using user credentials (built-in provider).
Apigee Integrated Developer Portal can now be configured with any third-party identity provider that supports SAML (the integration feature is currently in Public Preview). Security Assertion Markup Language (SAML) is a standard protocol for enforcing Single Sign-On (SSO). SSO authentication using SAML enables users to log in to your Apigee Integrated Developer Portal(s), without having to create new accounts, by using their existing accounts registered with the Identity Provider. Users can log in using their centrally managed account credentials.
Configuring SAML as an Identity Provider for an Integrated Developer Portal offers the following benefits:
- Set up your developer program once and re-use it across multiple integrated portals. Choose your developer program when creating your Integrated Developer Portal. Easily update or change the developer program as requirements evolve.
- Take full control of user management
Connect your company SAML server to the Integrated Developer Portal. When users leave your organization and are deprovisioned centrally, they will no longer be able to authenticate with your SSO service to use the Integrated Developer Portal.
Note: SAML provider is in beta release for Apigee Developer Portal
To configure SAML provider, we need to configure service provider (Apigee) as well as identity provider (such as Auth0) as below
Configure the Service Provider (Apigee) :
- Select Publish > Portals in the side navigation bar to display the list of portals.
- Click Accounts on the portal landing page. Alternatively, you can select Accounts in the portal drop-down in the top navigation bar.
- Click the Authentication tab.
- In the Identity providers section, click the SAML provider type.
- Select the Enabled checkbox to enable the identity provider.
- Click Save.
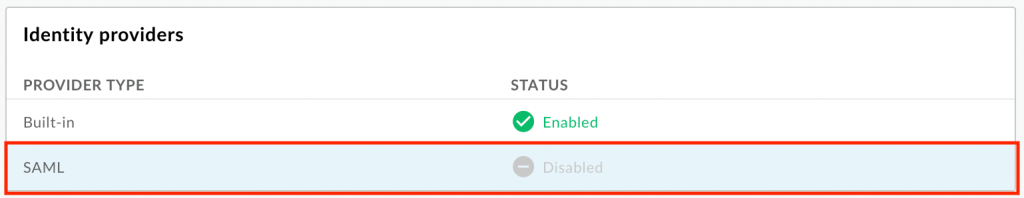
You will now be able to see SP metadata URL. Access it using the browser and open the downloaded xml file using any XML reader.

We need to fetch AssertionConsumerService URL from this file as below.
<md:AssertionConsumerService Binding=”urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST” Location=”https://diyyaedfgchrbui-a5vnmtygh8qzekbd.portal-login.apigee.com/saml/SSO/alias/diyyaumzqchrbui-a5vnmu1sp8qzekbd.apigee-saml-login” index=”0″ isDefault=”true”/>
This location value will be used while configuring the Identity Provider.
We also need to fill in the Sign-in URL , IdP entity ID in SAML settings, and upload a certificate in the Apigee SAML identity provider page. These we will fetch from Auth0 Identity Provider as below.
Configuring Identity provider Auth0 :
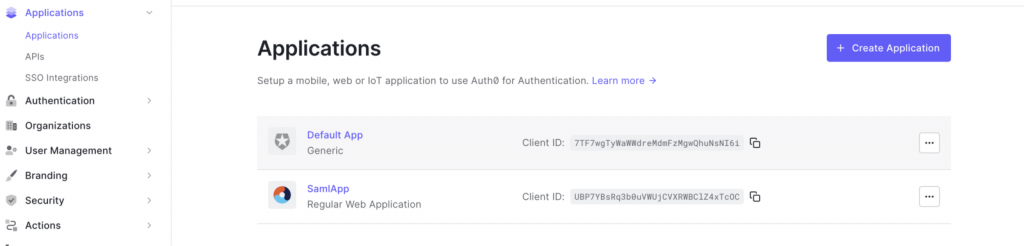
- Create Application under applications tab that can serve this SAML integration.
- Click on the newly created application, scroll to the Advanced Settings drop down menu and choose Certificates tab.
- Download the .pem file of the certificate and use it to upload to the Apigee SAML Identity Provider configuration.
- Under Add Ons tab on the Auth0 Applications page, enable SAML2 WEB APP
- On clicking SAML2 WEB you will get a pop-up that displays Issuer which will be IdP entity ID and Identity Provider Login URL will be Sign-in URL. Update these values on Apigee SAML Identity Provider configuration.
- Under the Settings tab of the SAML2 WEB APP pop-up, we will use the AssertionConsumerService URL value that we fetched earlier and use it as Application Callback URL.
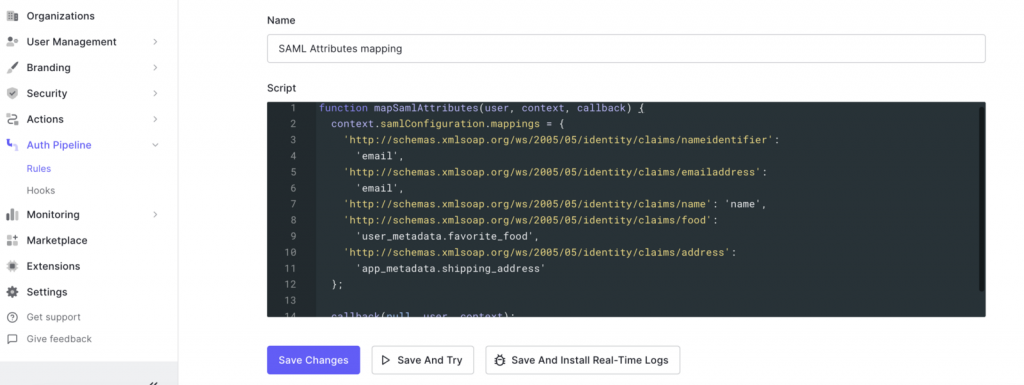
- Please note that Apigee requires the nameidentifier to be an email id. Hence we need to create a rule in Auth0 to map the attribute to email id instead of nameid, as shown below. This step might not be needed if other identity providers.
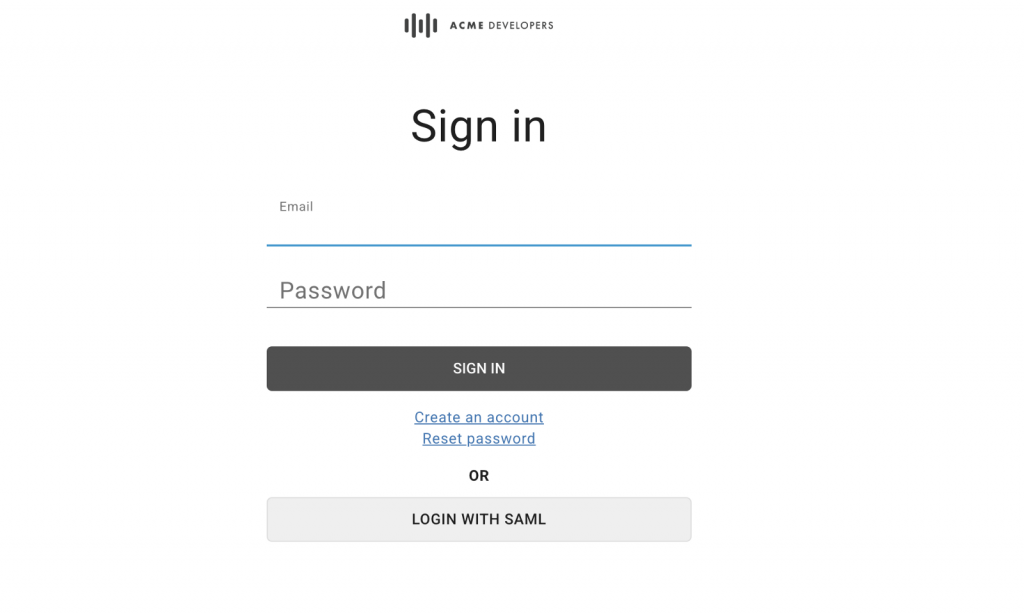
With this we are ready to test out the SAML integration. Launch your Apigee Integrated Developer Portal and click on sign in. We should see a Login with SAML option as below.
In case of any errors, trace the network using browser developer console and debug using Auth0 monitoring logs.
You can now disable the built-in identity provider (if required) as shown below
Disabling the built-in identity provider
To enable the built-in identity provider:
- Access the Built-in Identity Provider page.
- Click
 in the Provider Configuration section.
in the Provider Configuration section. - De-Select the Enabled checkbox to disable the identity provider.

Note: At least one identity provider must be enabled to allow users to sign in.
3. Click Save.
The original article published on Medium.

