By Kishore Jagannath.Jul 7, 2022
GCP IAM enables Organization and Project administrators to manage role based access to users on specific resources. Typically enterprises using Google cloud want to enforce strict controls on roles and permissions granted to individual users, groups or service accounts. Enterprises would want to enforce best practices of granting roles to user groups alone instead of individual users or service accounts.
In this article I will be presenting on of the methodologies to monitor the IAM role access within the GCP Cloud organisation through Cloud Log Alerts. As an example use case lets consider an example on how to configure log alerts when roles are assigned to users directly instead of user groups.
Step1:
In The GCP Logging Page lets filter based on Audit Logs to view all the changes that has happened on GCP resources.

Step 2:
Refine the Log filter to filter the audit logs and extract logs relevant to IAM Policy and role assignments.
logName=(“projects/<PROJECT_ID>/logs/cloudaudit.googleapis.com%2Factivity” ) AND protoPayload.methodName= “SetIamPolicy”
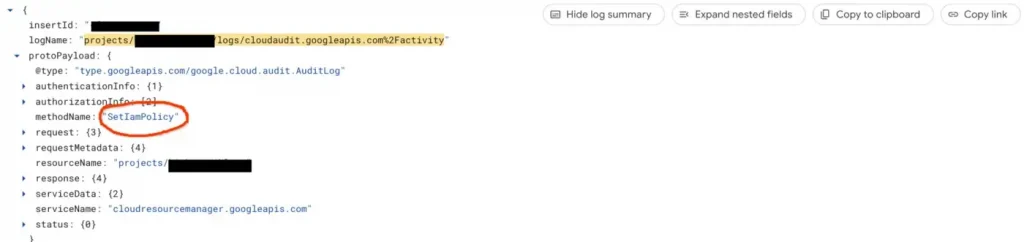
GCP Audit Log for IAM Role Assignments
Step 3:
Refine the log filter to filter audit logs for IAM role assignments when “users have been assigned to roles”
logName=(“projects/<<PROJECT_ID>>/logs/cloudaudit.googleapis.com%2Factivity” ) AND protoPayload.methodName= “SetIamPolicy” AND (protoPayload.serviceData.policyDelta.bindingDeltas.member: “user:”)
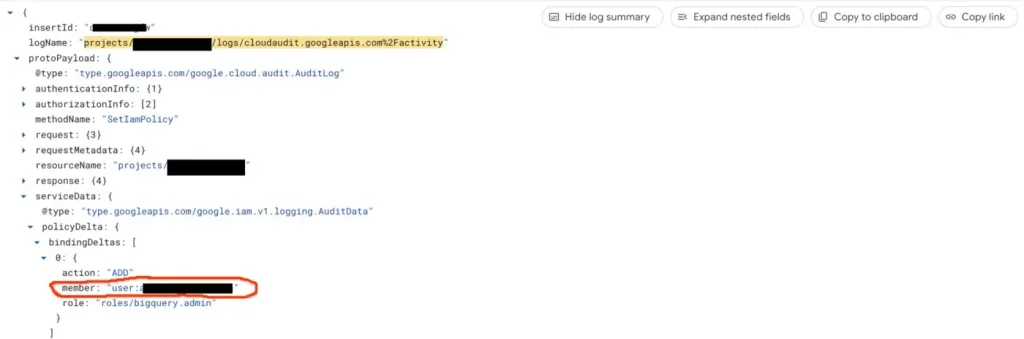
GCP Audit Log when roles are assigned to users
Step 4:
Create a log alert based on Log occurrence. With this configuration an alert will be triggered on the specified notification channel whenever an IAM policy is assigned to a user.
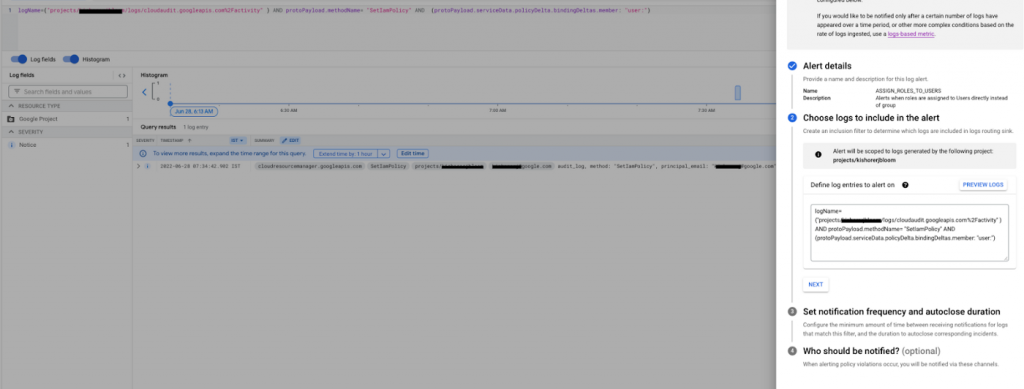
Conclusion
We showcased how to create Log alerts in GCP to track specific IAM role assignments. You can utilise this feature to get automatic alerts when non recommended practices like assigning roles to users directly or when roles are assigned to service accounts.
The original article published on Medium.
